Top 10 Security Tips That Will Keep You and Us Safe
Last updated: May 15, 2024

From the Omeda Privacy Office:
It’s easy to assume that scammers only target people who aren’t informed or act careless, but today’s cyber security threats are becoming more sophisticated and common. Bad actors are now excellent marketers and researchers, making cyber attacks harder to detect and prevent. The common phrase “This would never happen to me” is unfortunately no longer accurate and can in fact lead to less vigilance.
And because we know how much you rely on the trust of your customers, as we do here at Omeda, we put together our Top 10 Security Tips below to help all of us stay safe when using applications like the Omeda system, and also to keep your company, colleagues and customers safer and less vulnerable to the ever-expanding threats of cyber crime.
Upgrade your privacy game: Watch the webinar with our VP who shares crucial security insights:
1. Passwords
Think of passwords like house keys. You don’t use your office keys to open your home, which could allow others to easily access your private spaces and information. The same goes for the passwords you use to access your apps and accounts. Each should have a unique and hard-to-guess password, and you should avoid using easy-to-guess things like birthdays, maiden names, pet names etc., which someone could look up from your Social Media or professional profiles.
Here are some best practices for password creation and usage:
- Use strong, UNIQUE passwords for all accounts. NEVER reuse passwords across multiple accounts.
- Longer passwords are better! It’s a good idea to include a combination of both upper- and lower-case letters, numbers, and symbols, but a very long, easy-to-remember password (like a line from a favorite song) is better than a short, complicated one that you’ll be tempted to write down on a Post-It note. Password managers are helpful for safely storing your passwords, and many offer a secure password generator, in case you don’t want to have to create your own.
- Use two-factor authentication where possible, especially for accounts containing sensitive data (yes, it’s annoying, but what’s 10 more seconds that might just protect your lifetime savings?).
- Don’t use only dictionary words and often used passwords. Yes, some people actually use “Password123” as their login!
- Ask your Systems/IT team for a password manager app, or purchase one from the official app stores for personal devices to securely store your various passwords.
- Avoid using shared login services, e.g. logging in with your Google or Facebook account. If your original account gets compromised, bad actors now also have access to your accounts you granted access to with the compromised account.
2. Secure Network Connections (HTTPS/VPN)
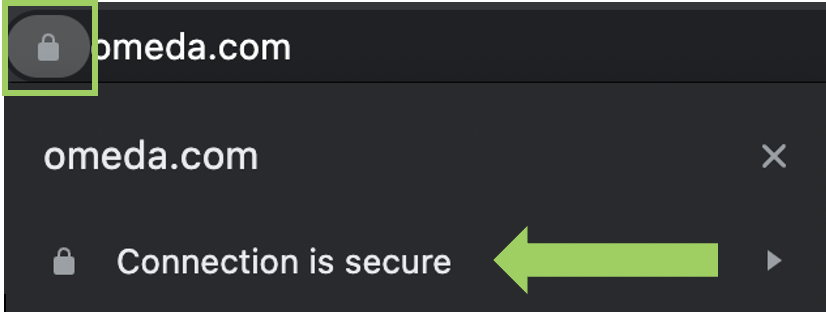
Never access any Websites that do not use a secure HTTPS connection. You can validate that this is the case by looking at the URL in your browser and verifying that it is secure through right-clicking on the URL/lock icon. Many browsers also now offer warnings via pop-ups or screens. This check is especially important when visiting websites from links in emails or on other websites to ensure that the connection remains secure.
Below is an example of verifying a secure connection:
Be very careful when connecting to public WiFi networks with shared/openly posted passwords, like in hotels, cafes and airports. Bad actors may intercept your connection and access sensitive data or credentials while you use a public network.
If you must use a public WiFi, use a VPN (Virtual Private Network) connection while connected to ensure that your connection is encrypted and secure. Your systems team can assist you with setting up a VPN on your work computer, or you can purchase an app through an official app store for personal use.
3. Suspicious Emails/Messages/Phone Calls
NEVER reply to calls or text messages from unknown numbers. As mentioned above, bad actors are great marketers and researchers, and many executives and employees have been duped by a late night email apparently coming from their CEO, or from a vendor to pay an overdue invoice, or to buy gift cards to send to a hot lead to close a deal. Bad actors scout social media and LinkedIn for posts indicating someone is at a conference, visiting a client, or on vacation, and will use that information shamelessly to appear legit.
In these types of scams, the first message sent is often used to establish a communication channel, which then will progressively ask for more information or action, leading up to further risk and potential incidents.
If in doubt, or if the message comes from an unknown number/email address or channel, reach out to the sender separately, using a known contact method (i.e. their company email, Slack or their office phone) to confirm if the message indeed originated from the sender. Or, contact your systems team or privacy office to validate that a message is legit.
Here is a real-life example of a phishing text message sent to an employee stating it came from the CEO of the company:
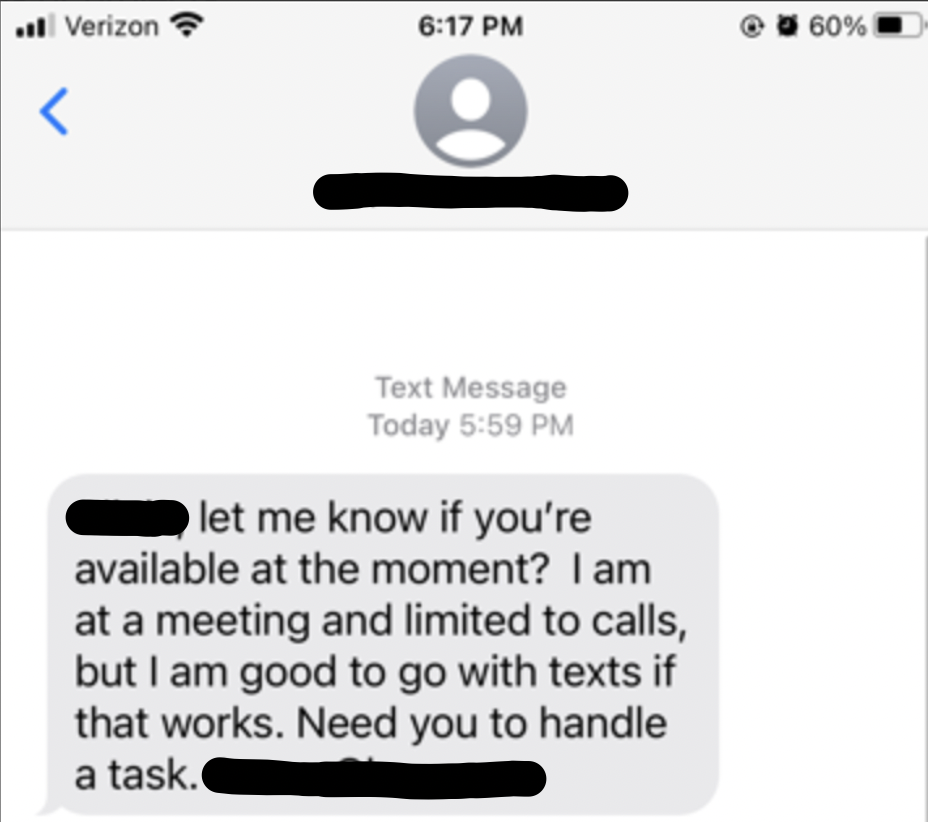
4. Unsafe Links and Attachments
NEVER open any attachments and links that might be included in suspicious messages or websites. User error/negligence is one of the leading causes of security incidents, and email is one of the top pathways bad actors use to gain unauthorized access to a user’s credentials or sensitive information. Always confirm with the sender separately, or contact your systems team or privacy office for guidance.
5. Safeguarding Sensitive Data
Data is often one of the company’s biggest assets, creating important revenue and keeping the business running. Therefore, think of your company’s and your personal data the same way you think about cash, checks or credit cards. You would not leave $100 unattended on the table at a coffee shop while using the restroom. The same goes for sensitive data – if someone can see or access it without your or your company’s consent, it’s at risk.
Always store sensitive data securely and never save or export data to a device or location that cannot be protected.
If you must print out information or receive mail with name, addresses, account numbers or similar, always destroy the hardcopies using secure shredding or document disposal services.
Dumpster diving is a thing, and here are some of the items bad actors use to put together research for a sophisticated attack with real-life scenarios, retrieved from vacation schedules, org charts, and more:

6. Installing Applications
Only install applications to your devices that came from reputable sources, like the official app stores or provider websites, or that have been approved by your company. Never install applications or programs that came from third-party websites or where you cannot validate the source, as they can contain malicious code that can compromise your device and allow a bad actor to gain unauthorized access.
When in doubt, please contact your systems or IT team for approval.
7. Backups
Always store your data in a secure location and ensure that sensitive and important data is backed up frequently, in case of device or data losses. Your systems/IT team, or your device vendor, can assist you in procuring the right service.
Never store sensitive or personal data on your desktop or on an unsecured device, memory stick, external drive, etc. Bad actors often steal devices they assume allow them easy access to data that can aid them in larger attacks.
8. Device Protection
This brings us to the topic of device protection. Always secure any device with a strong password, and/or biometric or two-factor authentication. Your computer or phone is a treasure-trove for bad actors, as it often contains a multitude of personal and sensitive information in a single place.
Chances are, if a bad actor can get into your device, they can get into your personal and company accounts.
Also, NEVER leave your office keycards, computer or device unattended, even in places you feel save. It is not uncommon that bad actors gain access to offices unnoticed, or grab your unsupervised backpack from under a table at a bar or restaurant.
9. Software Updates
Most software providers work hard to patch vulnerabilities and security risks discovered in their applications and programs. Therefore, keeping your applications up-to-date to ensure that you have the latest version will prevent bad actors from exploiting known security loopholes present in outdated versions of software and applications.
Contact your systems or IT team for support with updates when in doubt, or if you need assistance.
10. Incident Reporting
Anytime you come across a suspicious activity, message, or similar, contact your systems/IT team or privacy office IMMEDIATELY before taking any further action. The saying “Rather safe than sorry” has never been more relevant than in keeping yourself, your organization, and your partners and customers safe.
For questions about security in the Omeda application or Omeda’s Privacy Office, please contact privacy@omeda.com.
Subscribe to our newsletter
Sign up to get our latest articles sent directly to your inbox.
What you should do now
- Schedule a Demo to see how Omeda can help your team.
- Read more Marketing Technology articles in our blog.
- If you know someone who’d enjoy this article, share it with them via Facebook, Twitter, LinkedIn, or email.